How to hack mt4 server
I wish I posted here earlier, it would have saved me a lot of searching. Thank you :) if it's a legitimate reputable company then I wouldn't worry about it.
Actual forex bonuses
Hacking live MT4 account
I came across a order entry management software called 4xspinner (google as I don't know if links here are cool) and they require you to add your MT4 account number for licencing purposes.
Given my live account number makes me think twice but they don't have my password so I think this is ok, but I know nothing about programming and the technical side. I was wondering if it is in anyway that this program can link my live account for hacking purposes or my privacy can be invaded?
I came across a order entry management software called 4xspinner (google as I don't know if links here are cool) and they require you to add your MT4 account number for licencing purposes.
Given my live account number makes me think twice but they don't have my password so I think this is ok, but I know nothing about programming and the technical side. I was wondering if it is in anyway that this program can link my live account for hacking purposes or my privacy can be invaded?
If it's a legitimate reputable company then I wouldn't worry about it.
In theory, if they did intend to hack their way into your account (which I doubt), then knowing your account number helps.
I think the account number is only to run on one account, since it's a paid EA.
There are free visual traders available. E.G.
Https://www.Youtube.Com/watch?V=wexr8poqya4 (post links using the button just left of the normal text pull down.
If it's a legitimate reputable company then I wouldn't worry about it.
In theory, if they did intend to hack their way into your account (which I doubt), then knowing your account number helps.
Yes, it's doubtful but still crossed my mind, thanks for the advice :)
I think the account number is only to run on one account, since it's a paid EA.
There are free visual traders available. E.G.
Https://www.Youtube.Com/watch?V=wexr8poqya4 (post links using the button just left of the normal text pull down.
I wish I posted here earlier, it would have saved me a lot of searching. Thank you :)
If it's a legitimate reputable company then I wouldn't worry about it.
In theory, if they did intend to hack their way into your account (which I doubt), then knowing your account number helps.
So can a MT4 'expert advisor' indicator provide my trading actions or account information to anyone outside or is this not possible?
So can a MT4 'expert advisor' indicator provide my trading actions or account information to anyone outside or is this not possible?
If the expert doesn't use any DLL's, then the only way it can do that is via the built-in email/ftp clients, and those are under your control (just open tools > options > email/publisher tabs. Make sure email/ftp are disabled or contain your account details).
But if an expert uses an external DLL then it's possible (although still very unlikely in my opinion. I have never heard of anybody putting malicious code into a DLL intended for MT4 platform).
Server
This tab contains the most important settings changes in which can cause serious troubles in the terminal operation as far as the full disconnection. The client terminal is initially configured in the way providing normal, trouble-free operation. Thus, it is highly recommended not to change any parameters in this window needlessly.
In the "settings – server" window, it is possible:
Server #
Practically, the entire work of the client terminal is based on data (news and quotes) continuously incoming from the server. If a client terminal does not receive quotes, it is impossible to trade with it. In such a mode, the terminal allows just to analyze the existing data with indicators and line studies and test expert advisors. This situation can emerge for a number of reasons, one of them is incorrect setting of the server connection.
For connecting the client terminal to the server, the exact server IP address (or domain name) and port must be known. After the program has been installed, all these data will be specified, there is usually no need to change them. However, if there is a need to connect to another server, its address and port must be given in the "server" field. The data must be given in the following format: "[internet address of the server] : [port number]" (without spaces). For example: "192.168.0.1:443", where "192.168.0.1" is the server address, and "443" is the port number. After the data have been input, the "OK" button must be pressed.
The newly set server address and port number are stored on the hard disk. These data do not influence the operation of the client terminal until an attempt to open a new account is made. It is this moment when the terminal starts using of these given address and port number. The new server address will be added to the list of servers during account registration, and it can be chosen. If connection to the server succeeds, the new account will be opened. Otherwise, it is recommended to check all settings and try to reconnect.
Attention: incorrect connection setting is not the only reason for which a new account cannot be opened.
Proxy server #
Connection to internet through a proxy server can be another reason for which the server cannot be connected to. A proxy server is an intermediate between the trader's computer and the trading server. It is mostly used by internet providers or by local networks. If a connection problem occurs, you should turn to your systems administrator or to the internet provider. If a proxy is used, the terminal must be set up in a corresponding way. Setting of "enable proxy server" checkbox will enable proxy server support and activate the "proxy. " button. Pressing of this button will open the window where proxy server parameters should be specified (these data can be given by the systems administrator or by internet provider):
- Server – proxy server address and type (HTTP, SOCKS5, or SOCKS4);
- Login – a user login for access to the proxy server. If login is not needed, this field must remain empty;
- Password – a password for access to the proxy server. If password is not needed, this field must remain empty.
After the parameters have been specified, it is recommended to press the "test" button to check how the settings work. If they have been tested successfully, the "OK" button must be pressed in order the settings to be effective. Error message means that the proxy server was set up incorrectly. To find out about the reasons, the system administrator or internet provider must be contacted again.
Account and login #
Client terminal can connect to the server and work only using an account. There are login (the account number), master and investor passwords in the client terminal. To be authorized, one needs an account number and one of two passwords. The master password allows the full access to the account, while the investor one gives only a limited access. Being authorized with the investor password gives the right to look through charts, perform technical analysis and test expert advisors, but not trade. Investor password is a convenient tool showing the trading process at this given account.
After the account has been opened and if "keep personal settings and data at startup" option is enabled, its data (number, master and investor passwords) will be stored at the hard disk. At the program restart, these data will be used to connect the account automatically. If the option is disabled, a password must be entered manually at each restart of the terminal. Also if you disable this option, the information about previously used account and saved passwords will be deleted upon the next restart of the terminal .
The current account number and password are specified in the fields of "login" and "password". Data of another account can be input in these fields, then, after the "OK" button has been pressed, the terminal will try to authorize it. If authorization was not successfully completed, the data given should be checked and re-authorized. If this does not help, the technical support service should be contacted.
Having pressed the "change" button, one can specify new passwords in the window appeared. Doing so, one has to know the current password. It can be found in the message sent from the server after registration of a demo account. The new password is input in the corresponding field. If the "change investor (read only) password" option is enabled, the investor (not master) password will be changed.
Data export through DDE protocol #
Quotes delivered to the terminal can be exported to other applications through "DDE" (dynamic data exchange) protocol. To enable export of quotes, the "enable DDE server" option must be enabled and the "OK" button must be pressed. Data delivery will start immediately. More details about export of quotes can be found in the corresponding section.
Terminal allows to receive financial news promptly. They start to income just after connection to the server. No news issued when the terminal was disconnected will income in it. To enable news delivering, it is necessary to flag "enable news". In the "terminal" window, the "news" tab will appear in which news will be delivered as they are issued.
Attention: if the "enable news" option is enabled, but no news were issued, the "news" tab will not appear in the "terminal" window.
How to hack metatrader to create the ultimate risk:reward ratio tool

How to hack metatrader to create the ultimate risk:reward ratio tool
How to change metatrader to get the best risk:reward ratio tool
We talked about why the risk:reward ratio is one of the most important concepts in trading and how you should use it to make better trading decisions and easily increase your trading performance. Now is the time to show you how to visual the risk:reward ratio on your charts to help you make better trading decisions. The fibonacci tool is ideal to use it as a risk:reward ratio tool because it works with ratios and if you are a metatrader user, you can even modify the ratios on your fibonacci tool. In the following article we show you step by step how to turn your fibonacci tool into the ultimate risk:reward ratio gadget.
Be aware that if you change the settings of the fibonacci tool, it will not show you the actual fibonacci levels anymore and you have to change the parameters again before you can use the fibonacci levels!
Step 1: where is the fibonacci tool?
When you open your metatrader platform, you find the fibonacci tool in the menu bar at the top. If you cannot see it go to insert > fibonacciв > retracements

Step 2: reset the fibonacci tool
After you have selected the fibonacci retracements, drag it to the current chart. For now you do not have to worry where to put it, this just serves the purpose to turn the fibonacci retracements into a risk:reward ratio tool. After you put the fibonacci on your chart, a window like the one below will open. In the first step, you have to select each item on the left (0 вђ“ 0.0 | 0.236 вђ“ 23.6 |вђ¦) and delete every item from the list until the window is empty.

Step 3: add the risk:reward ratio parameters
After you have deleted all previous entries, you are ready to enter the new values for the risk:reward ratio display. We provide you with sample data you can use the following:

Level
Description
The values you enter on the left under вђњlevelвђќ define the distance. For example, the level of 0 defines the place of your stop loss. The value вђњlevelвђќ 1 is the place of your entry. The fibonacci toll will then use the distance between your stop loss order and your entry to calculate the other risk:reward levels.
The values you enter on the right under вђњdescriptionвђќ is going to be the text you see on your charts with the riskr:reward levels. The code вђњ%$вђќ means that metatrader will show the actual price next to the risk:reward ratio level.
Step 4: see the risk:reward ratio tool in action
You are done and are ready to use the risk:reward ratio tool on your charts. First, click the fibonacci retracement icon again to select the tool. Then go over to your chart and click on your entry (or potential entry), hold the mouse and drag the tool to the place of your stop loss order and release it. Done! You can now see the different risk:reward ratio levels on your charts.

Change back to fibonacci levels
If you want to change back to your fibonacci levels, delete all the risk:reward ratio levels as done in step 2 and add the actual fibonacci levels similar to step 3, but use the following parameters.
| Level | description |
| 0 | 0.0 -%$ |
| 0.146 | 14.6 -%$ |
| 0.236 | 23.6 -%$ |
| 0.382 | 38.2 -%$ |
| 0.5 | 50.0 -%$ |
| 0.618 | 61.8 -%$ |
| 0.786 | 78.6 -%$ |
| 0.942 | 94.2 -%$ |
| 1.0 | 100 -%$ |
Why do you care so much about risk:reward ratio?
We talkedв about the risk:reward ratio a couple of times and you can get more information why it is one of the most important trading concepts by reading the following articles:
– the holy grail: risk reward ratio and how to use it
How to hack a web server
Customers usually turn to the internet to get information and buy products and services. Towards that end, most organizations have websites.Most websites store valuable information such as credit card numbers, email address and passwords, etc. This has made them targets to attackers. Defaced websites can also be used to communicate religious or political ideologies etc.
In this tutorial, we will introduce you toweb servers hacking techniques and how you can protect servers from such attacks.
Web server vulnerabilities
A web server is a program that stores files (usually web pages) and makes them accessible via the network or the internet. A web server requires both hardware and software. Attackers usually target the exploits in the software to gain authorized entry to the server. Let’s look at some of the common vulnerabilities that attackers take advantage of.
- Default settings– these settings such as default user id and passwords can be easily guessed by the attackers. Default settings might also allow performing certain tasks such as running commands on the server which can be exploited.
- Misconfigurationof operating systems and networks – certain configuration such as allowing users to execute commands on the server can be dangerous if the user does not have a good password.
- Bugs in the operating system and web servers– discovered bugs in the operating system or web server software can also be exploited to gain unauthorized access to the system.
In additional to the above-mentioned web server vulnerabilities, the following can also led to unauthorized access
- Lack of security policy and procedures– lack of a security policy and procedures such as updating antivirus software, patching the operating system and web server software can create security loop holes for attackers.
Types of web servers
The following is a list of the common web servers
- Apache– this is the commonly used web server on the internet. It is cross platform but is it’s usually installed on linux. Most PHP websites are hosted on apache servers.
- Internet information services (IIS)– it is developed by microsoft. It runs on windows and is the second most used web server on the internet. Most asp and aspx websites are hosted on IIS servers.
- Apache tomcat – most java server pages (JSP) websites are hosted on this type of web server.
- Other web servers – these include novell's web server and IBM’s lotus domino servers.
Types of attacks against web servers
Directory traversal attacks– this type of attacks exploits bugs in the web server to gain unauthorized access to files and folders that are not in the public domain. Once the attacker has gained access, they can download sensitive information, execute commands on the server or install malicious software.
- Denial of service attacks– with this type of attack, the web server may crash or become unavailable to the legitimate users.
- Domain name system hijacking – with this type of attacker, the DNS setting are changed to point to the attacker’s web server. All traffic that was supposed to be sent to the web server is redirected to the wrong one.
- Sniffing– unencrypted data sent over the network may be intercepted and used to gain unauthorized access to the web server.
- Phishing– with this type of attack, the attack impersonates the websites and directs traffic to the fake website. Unsuspecting users may be tricked into submitting sensitive data such as login details, credit card numbers, etc.
- Pharming– with this type of attack, the attacker compromises the domain name system (DNS) servers or on the user computer so that traffic is directed to a malicious site.
- Defacement– with this type of attack, the attacker replaces the organization’s website with a different page that contains the hacker’s name, images and may include background music and messages.
Effects of successful attacks
- An organization’s reputation can be ruined if the attacker edits the website content and includes malicious information or links to a porn website
- The web server can be used to install malicious software on users who visit the compromised website. The malicious software downloaded onto the visitor’s computer can be a virus, trojan or botnet software, etc.
- Compromised user data may be used for fraudulent activities which may lead to business loss or lawsuits from the users who entrusted their details with the organization
Web server attack tools
Some of the common web server attack tools include;
- Metasploit– this is an open source tool for developing, testing and using exploit code. It can be used to discover vulnerabilities in web servers and write exploits that can be used to compromise the server.
- Mpack– this is a web exploitation tool. It was written in PHP and is backed by mysql as the database engine. Once a web server has been compromised using mpack, all traffic to it is redirected to malicious download websites.
- Zeus– this tool can be used to turn a compromised computer into a bot or zombie. A bot is a compromised computer which is used to perform internet-based attacks. A botnet is a collection of compromised computers. The botnet can then be used in a denial of service attack or sending spam mails.
- Neosplit – this tool can be used to install programs, delete programs, replicating it, etc.
How to avoid attacks on web server
An organization can adopt the following policy to protect itself against web server attacks.
- Patch management– this involves installing patches to help secure the server. A patch is an update that fixes a bug in the software. The patches can be applied to the operating system and the web server system.
- Secure installation and configuration of the operating system
- Secure installation and configuration of the web server software
- Vulnerability scanning system– these include tools such as snort, nmap, scanner access now easy (SANE)
- Firewalls can be used to stop simple dos attacks by blocking all traffic coming the identify source IP addresses of the attacker.
- Antivirus software can be used to remove malicious software on the server
- Disabling remote administration
- Default accounts and unused accounts must be removed from the system
- Default ports & settings (like FTP at port 21) should be changed to custom port & settings (FTP port at 5069)
Hacking activity: hack a webserver
In this practical scenario, we are going to look at the anatomy of a web server attack. We will assume we are targeting www.Techpanda.Org. We are not actually going to hack into it as this is illegal. We will only use the domain for educational purposes.
What we will need
- A target www.Techpanda.Org
- Bing search engine
- SQL injection tools
- PHP shell, we will use dk shell http://sourceforge.Net/projects/icfdkshell/
Information gathering
We will need to get the IP address of our target and find other websites that share the same IP address.
We will use an online tool to find the target’s IP address and other websites sharing the IP address
- Enter the URL https://www.Yougetsignal.Com/tools/web-sites-on-web-server/ in your web browser
- Enter www.Techpanda.Org as the target
- Click on check button
- You will get the following results
Based on the above results, the IP address of the target is 69.195.124.112
We also found out that there are 403 domains on the same web server.
Our next step is to scan the other websites for SQL injection vulnerabilities. Note: if we can find a SQL vulnerable on the target, then we would directly exploit it without considering other websites.
- Enter the URL www.Bing.Com into your web browser. This will only work with bing so don’t use other search engines such as google or yahoo
- Enter the following search query
HERE,
- “ip:69.195.124.112” limits the search to all the websites hosted on the web server with IP address 69.195.124.112
- “.Php?Id=” search for URL GET variables used a parameters for SQL statements.
You will get the following results
As you can see from the above results, all the websites using GET variables as parameters for SQL injection have been listed.
The next logic step would be to scan the listed websites for SQL injection vulnerabilities. You can do this using manual SQL injection or use tools listed in this article on SQL injection.
Uploading the PHP shell
We will not scan any of the websites listed as this is illegal. Let’s assume that we have managed to login into one of them. You will have to upload the PHP shell that you downloaded from http://sourceforge.Net/projects/icfdkshell/
- Open the URL where you uploaded the dk.Php file.
- You will get the following window
- Clicking the symlink URL will give you access to the files in the target domain.
Once you have access to the files, you can get login credentials to the database and do whatever you want such as defacement, downloading data such as emails, etc.
How to hack a webserver
Customers usually address the web to urge information and buy products and services. Towards that end, most organizations have websites. Most websites store valuable information like mastercard numbers, email addresses, and passwords, etc. This has made them targets to attackers. Defaced websites also can be wont to communicate religious or political ideologies etc.
In this tutorial, we’ll introduce you to web servers hacking techniques and the way you’ll protect servers from such attacks.
Web server vulnerabilities
A web server may be a program that stores files (usually web pages) and makes them accessible via the network or the web . An internet server requires both hardware and software. Attackers usually target the exploits within the software to realize authorized entry to the server. Let’s check out a number of the common vulnerabilities that attackers cash in of.
* default settings–
These settings like default user id and passwords are often easily guessed by the attackers. Default settings may additionally allow performing certain tasks like running commands on the server which may be exploited.
*misconfiguration of operating systems and networks –
Certain configurations like allowing users to execute commands on the server are often dangerous if the user doesn’t have an honest password.
* bugs within the OS and web servers–
Discovered bugs within the OS or web server software also can be exploited to realize unauthorized access to the system.
In addition to the above-mentioned web server vulnerabilities, the subsequent also can lead to unauthorized access
* lack of security policy and procedures–
Lack of a security policy and procedures like updating antivirus software, patching the OS and web server software can create security loopholes for attackers.
A)apache:
This is often the commonly used web server on the web. It’s cross-platform but is it’s usually installed on linux. Most PHP websites are hosted on apache servers.
B)internet information services (IIS)–
It is developed by microsoft. It runs on windows and is that the second most used web server on the web. Many asp and aspx websites are hosted on IIS servers.
C)apache tomcat –
Most java server pages (JSP) websites are hosted on this sort of web server.
* other web servers –
These encompass novell’s web server and IBM’s lotus domino servers.
Types of attacks against web servers
* directory traversal attacks–
This type of attack exploits bugs within the webserver to realize unauthorized access to files and folders that aren’t within the property right. Once the attacker has gained access, they will download sensitive information, execute commands on the server, or install malicious software.
* denial of service attacks–
With this sort of attack, the online server may crash or become unavailable to legitimate users.
* domain name system hijacking –
With this sort of attacker, the DNS setting is changed to point to the attacker’s web server. All traffic that was alleged to be sent to the online server is redirected to the incorrect one.
* sniffing–
Unencrypted data sent over the network could also be intercepted and wont to gain unauthorized access to the online server.
* phishing–
With this sort of attack, the attack impersonates the websites and directs traffic to the fake website. Unsuspecting users could also be tricked into submitting sensitive data like login details, mastercard numbers, etc.
* pharming–
With this type of attack, the attacker compromises the name system ( DNS) servers or on the user computer in order that traffic is directed to a malicious site.
* defacement–
With this sort of attack, the attacker put back the corporation’s website with a special page that contains the hacker’s name, images and should include background music and messages.
* an organization’s reputation is often ruined if the attacker edits the web site content and includes malicious information or links to a porn website.
* the online server is often wont to install malicious software on users who visit the compromised website. The malicious software downloaded onto the visitor’s computer is often an epidemic, trojan or botnet software, etc.
* compromised user data could also be used for fraudulent activities which can cause business loss or lawsuits from the users who entrusted their details with the organization.
Web server attack tools
Some of the regular web server attack tools include;
*metasploit–
This is often an open-source tool for developing, testing and using exploit code. It is often wont to discover vulnerabilities in web servers and write exploits which will be wont to compromise the server.
*mpack–
This is often an internet exploitation tool. It had been written in PHP and is backed by mysql because of the database engine. Once an internet server has been compromised using mpack, all traffic thereto is redirected to malicious download websites.
This tool is often wont to turn a compromised computer into a bot or zombie. A bot may be a compromised computer that is employed to perform internet-based attacks. A botnet may be a collection of compromised computers. The botnet can then be utilized in a denial of service attack or sending spam emails.
*neosplit –
This tool is often wont to install programs, delete programs, replicating it, etc.
How to avoid attacks on webserver
An organization can adopt the subsequent policy to guard itself against webserver attacks.
* patch management– this involves installing patches to assist secure the server. A patch is an update that fixes a bug within the software. The patches are often applied to the OS and therefore the webserver system.
* secure installation and configuration of the OS
* secure installation and configuration of the online server software
* vulnerability scanning system– these include tools like snort, nmap, scanner access now easy (SANE)
* firewalls are often wont to stop simple dos attacks by blocking all traffic coming the identify source IP addresses of the attacker.
* antivirus software are often wont to remove malicious software on the server
* disabling remote administration
* default accounts and unused accounts must be faraway from the system
* default ports & settings (like FTP at port 21) should be different to custom port & settings (FTP port at 5069)
Hacking activity: hack a webserver
In this practical scenario, we are getting to check out the anatomy of an internet server attack. We’ll assume we are targeting www.Techpanda.Org. We aren’t actually getting to hack into it as this is often illegal. We’ll only use the domain for educational purposes.
* A target www.Techpanda.Org
* bing program
* SQL injection tools
* PHP shell, we’ll use DK shell http://sourceforge.Net/projects/icfdkshell/
We will get to get the IP address of our target and find other websites that share an equivalent IP address.
We will use a web tool to seek out the target’s IP address and other websites sharing the IP address
*enter the URL https://www.Yougetsignal.Com/tools/web-sites-on-web-server/ in your browser
*enter www.Techpanda.Org because the target

Click on check button
you will get the subsequent results
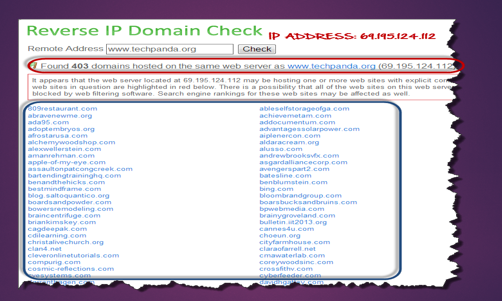
Based on the above outcomes, the IP address of the target is 69.195.124.112
We also acknowledged that there are 403 domains on an equivalent web server.
Our next step is to scan the opposite websites for SQL injection vulnerabilities. Note: if we will find a SQL vulnerable on the target, then we might directly exploit it without considering other websites.
* enter the URL www.Bing.Com into your browser. This may only work with bing so don’t use other search engines like google or yahoo
* enter the subsequent search query
IP:69.195.124.112 .Php?Id=
* “IP:69.195.124.112” limits the search to all or any the online sites hosted on the webserver with IP address 69.195.124.112
You will get the subsequent results

As you’ll see from the above results, all the websites using GET variables as parameters for SQL injection are listed.
The next logical step would be to scan the registered websites for SQL injection vulnerabilities. You’ll do that using manual SQL injection or use tools listed during this article on SQL injection.
Uploading the PHP shell:
We will not scan any of the websites listed as this is often illegal. Let’s assume that we’ve managed to login to one among them. You’ll need to upload the PHP shell that you simply downloaded from http://sourceforge.Net/projects/icfdkshell/
* unlock the URL where you uploaded the dk.Php file.
* you’ll get the subsequent window.

* clicking the symlink URL will offer you access to the files within the target domain.
Once you’ve got access to the files, you’ll get login credentials to the database and do whatever you would like defacement, downloading data like emails, etc.
How to hack mobile as a FTP server
How to hack mobile as a FTP server

What is FTP server ?
- File transfer protocol (FTP) may be a normal web protocol for transmittal files between computers on the net over TCP/IP connections.
- FTP may be a client-server protocol wherever a client can raise a file, and a neighborhood or remote server can offer it.
- The end-user machine is usually known as the native host machine, that is connected via the net to the remote host-which is that the second machine running the FTP software package.
- FTP could be a client-server protocol that depends on 2 communications channels between client and server: a command channel for the conversation and a data channel for transmitting file content.
- FTP helps sharing of files via remote computers with reliable and efficient reliable and data transfer.
- FTP uses a client-server architecture.
How to transfer files from website to webserver ?

OPTION 1: to load into FTP server
Considering, I got a certain website which I need to upload data / files into the server is using FTP client. FTP (file transfer protocol) is used to transfer data from one pc (your personal computer) to another pc (webserver). For example, since online casinos became very popular in india, we'll use it as an example. Casino review websites have to work really hard on their content so the user will be able to enjoy updated and rich content. One of the casinos is leovegas. One of the biggest review websites has a leovegas casino review page. Sites like that, often have to use FTP to transfer their content and files to the webserver. FTP client looks like file manager and you’ll be able to copy (upload, download) files here from one pc to another pc.

- Run filezilla client.
- First, you must add your website information: go to file - site manager:
- Click on new site button and add required information in general folder:
- Host - hostname of your website
- Server type - mostly FTP - file transfer protocol
- Logotype - normal
- User - your username
- Password - your password.
- Click on OK button to save the changes.
- Now information about your site are stored.
- You can connect your website (server) now.
- Click on file - site manager, select your site and click on connect button.
OPTION 2: using command terminal FTP.

- Type ftp to get into FTP mode.
- Type open (where ip address is the server’s network IP address) to open your connection to the FTP server.
- At this point, you’re asked for a username and password.
- For many FTP servers, using the username anonymous and your e-mail address as the password is enough to get you logged in. Some sites even permit you to log in without any username or password at all. On secure sites, however, you need to use a given username and password provided by the administrator of that specific server.
- Type lcd (where folder is a specific folder name) to change into the folder on your local drive that you want files to come to or from.
- Type the ls and cd commands to place yourself into the desired folder on the FTP server.
- Type the ascii or bin command to set your file transfer mode to ASCII or binary, respectively.
- This is important because choosing the wrong type will likely cause the transfer to fail. Unless it’s a plain-text file, continuously use binary mode.
- Type the get, mget, put, and mput commands to send or receive the desired files.
Learn ethical-hacking - ethical-hacking tutorial - FTP commands - ethical-hacking examples - ethical-hacking programs
This can be done via the command prompt also via the FTP command.
Read also
FTP server authentication :
- There are four different forms of ftp server authentication:
- Anonymous authentication
- Basic authentication
- Client certificate authentication
- Custom authentication
Anonymous authentication:
- The anonymous authentication requires the settings for anonymous access. This form of authentication permits access to an FTP site without a user account on your server or domain, and is most often used for public FTP sites.
Basic authentication:
- The basic authentication component specifies the settings for basic authentication. This form of authentication needs that user’s valid user accounts on your server or domain before they can log in.
Client certificate authentication:
Custom authentication:
- When custom authentication providers are added to FTP sites, the FTP service can attempt to authenticate a user with every custom authentication provider that’s enabled within the order that the providers are stated in the FTP configuration settings.
Anatomy of FTP – hack FTP server
1. Hack using website address: ( )

Learn ethical-hacking - ethical-hacking tutorial - hack using website address - ethical-hacking examples - ethical-hacking programs
Hack SSH server with nmap and hydra – pentest guide

Hello guys, this time I’m going to tell you how to hack SSH server connection with nmap and hydra.
Before we get started, let me remind of something: these penetration testing tutorials are only meant for educational purposes. Harming anyone elses machines but your own, is illegal.
Hack SSH server with nmap and hydra
Requirements for this tutorial:
- Hydra
- Nmap
- Wordlist
- Your own machine or virtual environment to test on
The first three are found in kali linux, you can use that if you’d like, I’m using debian with nmap and hydra installed.
Now lets get started with scanning the entire local network. We need to find SSH server with root login allowed on port 22. We will save all on a file called “ssh.Txt”
nmap -p22 -PN -sv -og ssh.Txt -open 192.168.2.1/24
this will scan your entire local networks SSH servers with port 22 open. I’m not going to show the output, because I will be using debian server installed on vmware.
You can scan almost anything with nmap, just learn to use it first, type nmap -h on terminal to see all the commands and their meanings.
Now let’s get to the cracking with hydra.
When we have the IP address or list of ip addresses we want to test, we can start the password testing.
We are going to test login root with the list of passwords and IP’s on port 22.
Hydra -l root -M /path/to/ip/list.Txt -P /path/to/passwordlist.Txt ssh

If you succeed the output on terminal will look similar to this image.
Congrats, you have learned how to penetrate your ssh server.
Summary for “hack SSH server with nmap and hydra”
Thank you for reading my entire post! �� be sure to follow me on social medias to get more awesome posts to read! And please share if you liked my post!
Metatrader 5 mini forum, answers, tips, tricks and glitches
Rate this app:
More details
| for android: 4.0.3 and up | guide: metatrader 5 cheats tutorial |
| when updated: 2018-03-19 | star rating: 4.5 |
| name: metatrader 5 hack for android | extension: apk |
| author: metaquotes software corp. | File name: net.Metaquotes.Metatrader5 |
| current version: 500.1777 | user rating: everyone |
| downloads: 1000000-5000000 | version: mod, apk, unlock |
| system: android | type: education |
Share metatrader 5 cheats guides hints and tutorials - best tactics from users below.
Metatrader 5 tricks and codes:
Add your tips
Hints and tips:
Glitches:
Codes:
Guide:
Easter eggs:
Advice for new users:
Please wait 10 seconds
Metatrader 5 hack cheats codes tips tricks advices for new users and Q&A!
Add your questions or answers
Q: how to get the best score?
Q: do you know more hacks or tricks?
Q: what is your strategy?
Watch metatrader 5 videoreviews, gameplays, videoinstructions, tutorials, guides, tips and tricks recorded by users, pro players and testers.
Metatrader 5 gameplay, trailers and related videos
Watch introduction to the metatrader 5 trading platform video.
Watch DO BETTER TECHNICAL ANALYSIS - A QUICK TIP IN METATRADER 5 (MT5) video.
Watch how to set up metatrader 5 video.
Watch MT5 "metatrader 5" overview tutorial video.
Watch metatrader 5: primeiro contato e as principais dúvidas video.
Watch aprendendo a usar o metatrader 5 video.
Watch metatrader 5 | MT5 | getting started signing up and following MQL signals video.
Watch winning forex trading strategy - $180 in 1 day on metatrader 4 video.
Watch metatrader 5 | MT5 | getting started at AMP futures video.
Watch review metatrader 5 for android video.
About the application:
Trade financial instruments: forex symbols, CFD, futures, options and stocks from your phone or tablet!Metatrader 5 is a platform for mobile online trading on the forex and stock markets. The application allows you to connect to brokers' servers, keep stock prices and currency quotes, analyze financial markets using charts and technical indicators, trade, and view the history of your trading operations. This is absolutely gratis and accessible anywhere in the world!TRADING* real-time quotes of financial instruments* full set of trade orders, including pending orders* level II prices with up to 32 quotes* all types of trade execution* detailed trading historyadvanced FUNCTIONALITY* quick switch between financial instruments on charts* sound notifications* customizable chart color scheme* trade levels visualizing the prices of pending order, as well as SL and TP values on the chart* gratis financial news — variety of materials everyday* chat with any registered MQL5.Community player* help for push notifications from the desktop metatrader 5 platform and MQL5.Community servicestechnical ANALYSIS* interactive real-time charts with zoom and scroll options* 30 most famous technical indicators* 24 analytical objects: lines, channels, geometric shapes, as well as gann, fibonacci and elliott programs* 9 timeframes: M1, M5, M15, M30, H1, H4, D1, W1 and MN* 3 types of charts: bars, japanese candlesticks and broken linedownload metatrader 5 for android device on your phone or smartphone and trade forex, CFD and futures instruments anytime and anywhere in the globe!
Metatrader 5 hack - gallery:
Changes in metatrader 5:
Reviews and recent comments:
Bres mel: suvath
user rated this game 5/5 on 2017-12-30
Ade yunus yanuar: exellent
user rated this game 5/5 on 2015-12-21
Siyabonga mthethwa: ������
user rated this game 5/5 on 2018-01-05
Mr .Nivelyy nivelyy: nice awesome apk
user rated this game 5/5 on 2016-02-03
Sandra aditya: good
user rated this game 5/5 on 2016-11-15
Navin chaudhary: gr8
user rated this game 5/5 on 2016-06-08
Arya D: loved it
user rated this game 5/5 on 2016-11-29
Jason rodrigues: device not supported. Samsung galaxy grand duos. Samsung galaxy grand duos. I just upgraded to 4.2.2 and now running mt5 says device not supported. I uninstalled the apk afer the make batter and then reinstalled it. Works ok now. Good apk.
User rated this game 5/5 on 2013-10-18
Anand tiwari: very awesome apks for trading
user rated this game 5/5 on 2017-09-02
Neville junior: good
user rated this game 5/5 on 2016-06-21
Israel luria: very simple simple to manage my acc and create deals. A tiny harder to use for technical analysis in the smartphone but that is to be expected. It would have been unbelievable if trend lines and another technical indicators I place in the desktop application were saved in a method that they be added here as well, so I wouldn't have to work twice.
User rated this game 5/5 on 2016-12-28
Ali alavi poor: best partner for to go trading first of all thanks to mofid brokerage company to have gut to be first in IRAN that provide people gratis platform with true time data. And meta trader, thanks, and well done
user rated this game 5/5 on 2016-10-11
Fredric harllee: wow
user rated this game 5/5 on 2014-01-16
Keenan jansen: awesome apk really awesome guys if your a awesome trader and you know what your doing i personally recomend!
User rated this game 5/5 on 2017-10-14
Zanele pzym28: good items
user rated this game 5/5 on 2017-11-18
Reza farshbaf zinati: it is a good tool.
User rated this game 5/5 on 2016-09-14
Fahad fraz: good present need add more features of the full ver to this android device ver
user rated this game 5/5 on 2016-09-19
Josip vukelja: very convenient
user rated this game 5/5 on 2017-03-05
Baah david: mt5 this android device mobile apk has taken over my laptop.
User rated this game 5/5 on 2016-11-21
Jermin dijkhoff: awsome
user rated this game 5/5 on 2017-10-10
Azinan deep: it's just nice ��
user rated this game 5/5 on 2017-12-09
Zia tareen: graet
user rated this game 5/5 on 2016-12-28
Mohd yusof mohd noor: good. ..
User rated this game 5/5 on 2017-12-23
A rajabi: thanks to meta quotes tool corporation.
User rated this game 5/5 on 2017-11-25
Sivakumar katta: awesome apk
user rated this game 5/5 on 2017-01-27
Asa zata: good apk
user rated this game 5/5 on 2017-12-13
Mayur soriya: nice apk
user rated this game 5/5 on 2016-08-32
Gary yang: love the modernize would be awesome if the mobile apk is able to help 2 charts at a time
user rated this game 5/5 on 2014-12-03
Sani abuba: it will assist
user rated this game 5/5 on 2017-08-13
Jerry mhlanga: quick and easy to use
user rated this game 5/5 on 2017-10-21
Omoyo moyo: greate apk wow!! Finally on lg g2!!
User rated this game 5/5 on 2013-12-30
Saber esfandiyari: ممنون
user rated this game 5/5 on 2016-05-12
Ndumiso thandazani: good appreciation I love the method it work it train even the juniors how to trade successful
user rated this game 5/5 on 2016-11-16
Vusi ndima: awesome platform, gives you immediate execution, simple to use, regular news feeds which makes trading good.
User rated this game 5/5 on 2017-06-10
Ehsan saeedy: excellent.
User rated this game 5/5 on 2015-01-29
It is excellent
user rated this game 5/5 on 2017-11-13
Nahnianurkasim inayahnia: naska hernawaty.Nur
user rated this game 5/5 on 2017-04-26
Jake gunvo: awesome
user rated this game 5/5 on 2017-11-11
Server hacking - how to hack web server ?
What is a web server ?
- A web server is a storage area, which in-turn a program,
- That stores files ( web pages, CSS scripts, images, java script files ) relevant to the websites in a secure folder.
- Control website and file access located in the server by the website users via the internet.
- Control sessions and maintain file access details
- Web server indicates both hardware and software.

Learn ethical hacking - ethical hacking tutorial - what is web server - ethical hacking examples - ethical hacking programs
How web server works ?

Learn ethical hacking - ethical hacking tutorial - how web server works - ethical hacking examples - ethical hacking programs
- HTTP (hyper text transfer protocol) is used to transfer web pages from a web server to web client (browser).
- Web pages are arranged in a directory structure in the web server.
- HTTP supports CGI (common gateway interface).
- Why HTTP is used in websites - the reason is, HTTP supports virtual hosting (hosting multiple sites on the same server).

Learn ethical hacking - ethical hacking tutorial - HTTP used in websites - ethical hacking examples - ethical hacking programs
Web server vulnerabilities
Attackers typically targets the exploits in the software part to enter into the server. Below are some of the possibility of attacking the server through wild guessing.
- Default settings of the server
- By default, the user name and passwords can be easily guessed by the attackers. For example, the default credentials for mysql is root (username) and the password is empty.
- Attackers may guess the default settings which might got some of the basic tasks to be performed in the server such as running commands on the server which can be exploited.
- Mistakes by the admin - misconfiguration
- Sometimes, by mistake administrators will give access roles to the users unknowingly which permits the way such as allowing users to execute commands on the server.
- Software bugs
- By default, the webserver may have bugs and this paves a way for the attackers to gain unauthorized access to the system.

Learn ethical hacking - ethical hacking tutorial - web server vulnerabilities - ethical hacking examples - ethical hacking programs
Types of web servers
- The following is a list of the common web servers
- Apache 45% - what is apache - it is free and open source and thus is in reach to many. It is cross platform but is it’s usually installed on linux. Most PHP websites are hosted on apache servers.
- Microsoft internet information services (IIS) 20% - what is IIS - microsoft’s product and its uses are increasing substantially. Websites designed with dotnet framework will be hosted inturn the web pages will have the extension of asp and aspx.
- Apache tomcat 20% - what is tomcat server - java web server - java server pages (JSP) websites will be hosted in this type of web server.
- NGINX 12% - what is nginx server - this web server is used to host large websites like facebook, twitter. The reason for using NGINX is because of its good multithreading capabilities.
- Other 5% - these include novell's web server and IBM’s lotus domino servers.

Learn ethical hacking - ethical hacking tutorial - types of web servers - ethical hacking examples - ethical hacking programs
Web server attack techniques

Learn ethical hacking - ethical hacking tutorial - web server attack techniques - ethical hacking examples - ethical hacking programs
- Denial of service attacks - what is DOS / DDOS - continuous hits on the web server. Using this type of attack, the web server may crash and the website will be down.

Learn ethical hacking - ethical hacking tutorial - denial of service attacks - ethical hacking examples - ethical hacking programs
- Domain name system hijacking - what is dns hijacking - repointing to attacker’s web server. So that, the users will go to the attacker’s website which may increase the number of hits for the newly redirected websites.
Learn ethical hacking - ethical hacking tutorial - domain name system hijacking - ethical hacking examples - ethical hacking programs
- Sniffing- what is sniffing - unencrypted data sent over the network may be intercepted and used to gain unauthorized access to the web server.

Learn ethical hacking - ethical hacking tutorial - sniffing - ethical hacking examples - ethical hacking programs
- Phishing - what is phishing attack - with this type of attack, the attack impersonates the websites and directs traffic to the fake website. Unsuspecting users may be tricked into submitting sensitive data such as login details, credit card numbers, etc.

Learn ethical hacking - ethical hacking tutorial - phishing - ethical hacking examples - ethical hacking programs
- Pharming - using this type of attacking, the attacker will compromise the domain name system (DNS) servers. So that, fake server IP will be given to the user PC and the user will be redirected to the fake server which is in the hands of a attacker.

Learn ethical hacking - ethical hacking tutorial - pharming - ethical hacking examples - ethical hacking programs
- Defacement - what is defacing a server - controlling the server by injecting the php shell scripts. Below are the activities can be done in the server.
- Injecting any kind of files
- Deleting server files and web pages
- Modifying the existing file
- Gaining access to the database servers through config files.
- Directory traversal attacks - accessing files and folders that are not in the public domain.

Learn ethical hacking - ethical hacking tutorial - directory traversal attacks - ethical hacking examples - ethical hacking programs
Web server attack prevention

Learn ethical hacking - ethical hacking tutorial - web server attack prevention - ethical hacking examples - ethical hacking programs
so, let's see, what we have: hi all, I came across a order entry management software called 4xspinner (google as I don't know if links here are cool) and they require you to ad at how to hack mt4 server
Contents of the article
- Actual forex bonuses
- Hacking live MT4 account
- Server
- Server #
- Proxy server #
- Account and login #
- Data export through DDE protocol #
- How to hack metatrader to create the ultimate...
- How to hack metatrader to create the ultimate...
- How to change metatrader to get the best...
- Step 1: where is the fibonacci tool?
- Step 2: reset the fibonacci tool
- Step 3: add the risk:reward ratio parameters
- Level
- Description
- Step 4: see the risk:reward ratio tool in action
- Change back to fibonacci levels
- Why do you care so much about risk:reward ratio?
- How to hack a web server
- Web server vulnerabilities
- Types of web servers
- Types of attacks against web servers
- Effects of successful attacks
- Web server attack tools
- How to avoid attacks on web server
- Hacking activity: hack a webserver
- How to hack a webserver
- Web server vulnerabilities
- * default settings–
- *misconfiguration of operating systems and...
- * bugs within the OS and web servers–
- * lack of security policy and procedures–
- A)apache:
- B)internet information services (IIS)–
- C)apache tomcat –
- * other web servers –
- Types of attacks against web...
- * directory traversal attacks–
- * denial of service attacks–
- * domain name system hijacking –
- * sniffing–
- * phishing–
- * pharming–
- * defacement–
- Web server attack tools
- How to avoid attacks on webserver
- Hacking activity: hack a...
- Uploading the PHP shell:
- How to hack mobile as a FTP server
- How to hack mobile as a FTP server
- What is FTP server ?
- How to transfer files from website to webserver ?
- OPTION 1: to load into FTP server
- OPTION 2: using command terminal FTP.
- FTP server authentication :
- Anonymous authentication:
- Basic authentication:
- Client certificate authentication:
- Custom authentication:
- Anatomy of FTP – hack FTP server
- 1. Hack using website address: ( )
- Hack SSH server with nmap and hydra – pentest...
- Hack SSH server with nmap and hydra
- Metatrader 5 mini forum, answers, tips, tricks...
- Rate this app:
- Metatrader 5 tricks and codes:
- Please wait 10 seconds
- Add your questions or answers
- Q: how to get the best score?
- Q: do you know more hacks or tricks?
- Q: what is your strategy?
- Metatrader 5 hack - gallery:
- Reviews and recent comments:
- Server hacking - how to hack web server ?
- What is a web server ?
- How web server works ?
- Web server vulnerabilities
- Types of web servers
- Web server attack techniques
- Web server attack prevention
No comments:
Post a Comment